Projects like Falco and Cilium Tetragon, based on eBPF threat detection, provide powerful features but require manual setup, fine-tuning, and ongoing maintenance. GuardDuty simplifies this process for teams operating within the AWS environment.
Telemetry data is captured from the data flow, enriched with relevant context (such as pod specifications, image identities, and namespaces), and subjected to GuardDuty’s detection mechanisms.
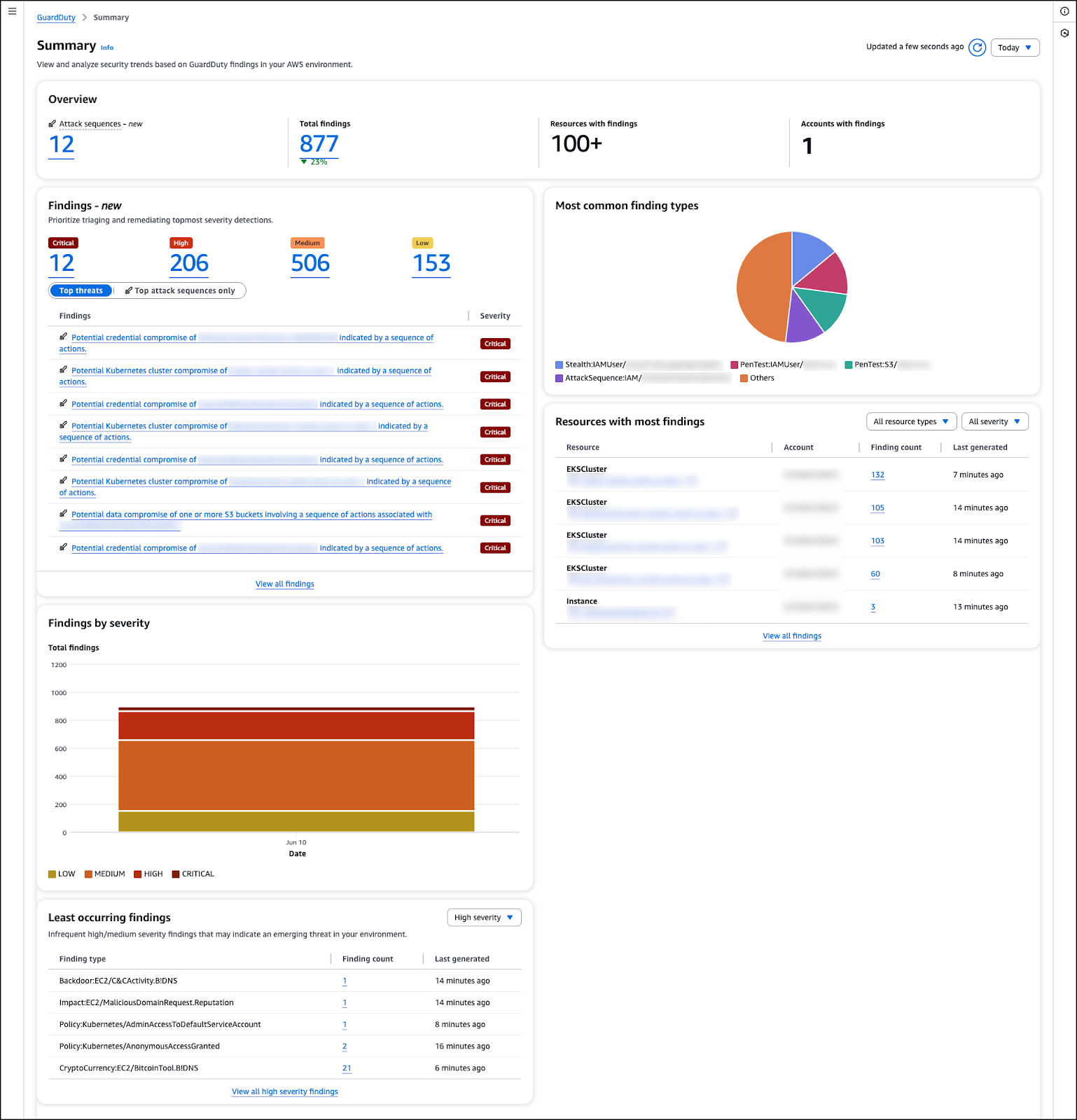
AWS has enhanced GuardDuty’s threat detection capabilities on EKS clusters by introducing new features for monitoring runtime performance. This includes a managed eBPF agent to identify potential threats at the container level. By focusing on system calls directly from the Kubernetes data flow, users now have the ability to flag suspicious activities like covert data exfiltration, unauthorized access, and stealthy cryptocurrency mining.
GuardDuty offers a unique hybrid approach by incorporating an agent, deployed as a DaemonSet in the EKS cluster, that is entirely managed by AWS. Users are relieved from the burden of configuring or supervising the agent. By operating independently of the application setup, GuardDuty avoids the complexities associated with sidecar or in-container setups, enabling users to gain a more detailed insight into container activities during runtime.
GuardDuty’s enhanced EKS extension aligns with a broader industry trend of integrating advanced threat detection features into managed infrastructure, reducing the dependence on users to set up agents. Microsoft Defender for Containers offers agent-free scanning for Azure Kubernetes Service (AKS), while Google Cloud’s Security Command Center integrates Kubernetes threat detection through Event Threat Detection (ETD).
Access to this feature is granted upon activation of EKS Protection or Runtime Monitoring.
The system consistently monitors system-level telemetry, scanning for suspicious or malicious behavior, and relaying findings to the GuardDuty console and EventBridge for seamless integration with incident response workflows.
The conventional agent-based approach to threat detection in Kubernetes has been scrutinized for its complexities, special permissions requirements, and susceptibility to cyber threats. Setting up agents can be cumbersome in managed environments and may consume essential node resources.
This strategic shift is not incidental. The 2024 State of Kubernetes Security Report underscores that complexity and setup obstacles are significant barriers to Kubernetes security solutions. GuardDuty’s Extended Threat Detection initiative reflects a move towards comprehensive, guided defense mechanisms aimed at alleviating complexities while ensuring detailed monitoring during runtime.
This solution is now part of a new wave of cloud-native security services that embed protection into workloads by seamless integrations within the infrastructure, eliminating the need for users to manually deploy agents.
AWS’s enhanced telemetry suite is designed to identify unusual binary activities, commonly used crypto-mining tools, network connections to suspicious entities, and potential data breaches.
Trailblazing companies like Orca Security and Wiz have adopted an agentless cloud security approach utilizing cloud APIs and snapshots instead of real-time probing. This method provides an overview of virtual machines, containers, storage, and IAM settings but may overlook on-the-fly behaviors necessitating deeper analysis at the OS level.